VoIP, SIP and SIP Trunking - The New Dial Tone.

A Short History: Stepping backwards in time lines used to be delivered on a set of two wires, per line, which required large copper cables to handle the number of lines a business needed. As technology progressed, businesses could upgrade to a T-1 service but it did not provide Caller ID information so the PRI displaced the T-1's over time. That brings us to 21st century. Today almost all communications are using some form of IP and there are various forms of IP called VoIP, SIP and SIP Trunking.
The one thing to note here is that it is imperative to have someone who understands the security risk of IP communications known as VoIP, SIP and SIP Trunking. Often providers solicit, and customers sign, documents without understanding the complexity of network issues. Hosted providers provide what the industry refers to a "ship and pray" standard. Customer call-ins for resolution issues have large amounts of hold times without resolution. Thus customers leave, 25% of all customers that go to the Cloud come back out and never want to experience that again.
When installing VoIP phones you need to consider the new network traffic about to be placed on the network or the risk factors of the data that can be, and often is compromised. Did you know that an average IP address is probed up to 300 times in a one hour time frame? Often technicians install a small residential router / firewall which does not have the capacity to handle these types of attacks. Understand this, that cheap routers may work, but they will get hacked.
VoIP Solutions Depend On A VoIP Security Solution Firewall
Cyber Security With Voice Priority
As professionals we take this topic of VoIP design, integration and ongoing security very seriously. When you connect your business communications to the Internet, you open up streams of data that provide lanes of information into and out of your network. Simple firewall routers are not adequate to protect your information from being hacked or compromised because they are time-stamped, don't automatically update and do not provide alerts when attacks are happening.
Built specifically to address the voip platform, we provide, configure and install Cyber Security routers that monitor the carrier broadband circuit, watch and learn from Internet probes and attacks, notify the other community of routers on the platform of the attacks and update as needed.
Another powerfull advantage of providing a router specific for VoIP needs is that it gives priority to the voice traffic. Not just a firewall designed to inspect and block traffic it allows for white listed IP addresses allowing traffic to pass-through, but give it priority should the circuit run into latency issues, fail over immediately to the LTE or another circuit.
SD Wan, VoIP Security &
Immediate LTE Failover
To understand SD Wan, you need to understand how SD Wan has evolved. In the perfect world you would have your own dedicated VPN network. MPLS addressed the need but is expensive to manage and maintain. Because of the complexity and cost, MPLS is quickly being replaced by SD Wan. Software Defined Wide Area Network allows for dynamic traffic routing to better optimize application performance over diverse networks.
Since SD Wan replaces MPLS, SD Wan allows network traffic to flow out one broadband provider one second and out another should it go off line. Taking advantage of that technology we deploy routers that allows and utilize multiple broadband connections.
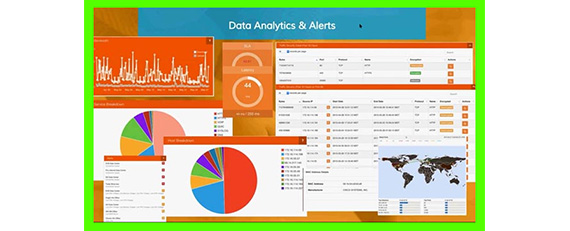
Is your business phone system an expense or a revenue generator?
When was the last time your business phone bill was audited? Are you over-provisioned? Are you spending too much? Do you know who is handling the majority of inbound and outbound traffic? Are calls being recorded if a service issue become present? If someone hacked into your phone system, would you be alerted? These are just a few of the questions we ask and then provide solutions that answers each of these questions.
With very little investment we can provide a cost effective solution for your business, call intelligence and detailed records, security for the communications platform and turn your phone system into revenue generating platform.